
With so much money flowing throughout casinos, these establishments are a highly-regulated world within themselves when it comes to security.
One of the most critical areas of casino security is physical key control because these instruments are used for access to all of the most-sensitive and highly-secured areas, including counting rooms and drop boxes. Therefore, the rules and regulations that relate to key control are extremely important to maintaining tight control, while minimizing loss and fraud.

Casinos that are still using manual logs for key control are at constant risk. This approach is prone to many natural uncertainties, such as vague and illegible signatures, damaged or lost ledgers, and time-consuming write-off processes. More annoyingly, the labor intensity of locating, analyzing and investigating keys from a large number of registers is very high, putting tremendous pressure on key auditing and tracking, making it difficult to accurately perform key tracing while negatively impacting compliance.
When choosing a key control and management solution that meets the needs of the casino environment, there are important features to consider.

1.User Permission Role
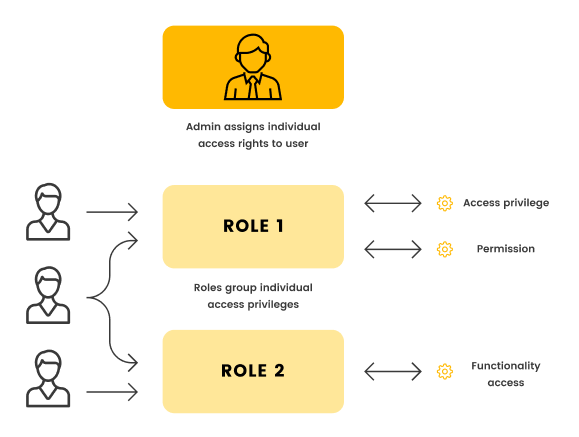
Permission roles grant users with role management privileges administrative privileges to system modules and access to restricted modules. Therefore, it is completely necessary to customize the role types that are more applicable to the casino in the middle range of permissions for both administrator and normal user roles.
2. Centralized key management
Centralizing a large number of physical keys, locked in secure and robust cabinets according to predetermined rules, makes key management more organized and visible at a glance.

3. Locking Keys Individually
Coin machine coin cabinet keys, coin machine door keys, coin cabinet keys, kiosk keys, currency receiver coin box contents keys and currency receiver coin box release keys are all locked separately from each other in the key control system
4. Key Permissions are configurable
Access control is one of the most fundamental claims of key management, and access to unauthorized keys is an important area that is regulated. In a casino environment, characteristic keys or key groups should be configurable. Instead of a blanket "all keys are free to access as long as they enter a sealed space", the administrator has the flexibility to authorize users for individual, specific keys, and it can completely control "who has access to which keys". For example, only employees authorized to drop off currency receiver coin boxes are allowed to access currency coin box release keys, and these employees are prohibited from accessing both currency receiver coin box contents keys and currency receiver coin box release keys.
5. Key Curfew
Physical keys must be used and returned at the scheduled time, and at the casino we always expect employees to return keys in their possession by the end of their shift and prohibit the removal of any keys during non-shift periods, usually associated with employee shift schedules, eliminating the possession of keys outside of the scheduled time.

6. Event or explanation
In the case of an event like a machine jam, customer dispute, machine relocation or maintenance, the user would typically be required to include a predefined note and freehand comment with an explanation of the situation before removing keys. As required by regulation, for unplanned visits, users should provide a detailed description, including the reason or purpose for which the visit occurred.
7. Advanced Identification Technologies
A well designed key management system should have more advanced identification technologies such as biometrics/retinal scanning/face recognition, etc. (avoid PIN if possible)
8. Multiple layers of security
Before accessing any key in the system, each individual user should face at least two layers of security. Biometric identification, a PIN or an ID card swipe to identify the user’s credentials are not enough separately. Multi-factor authentication (MFA) is a security method that requires users to provide at least two authentication factors (i.e. login credentials) to prove their identity and gain access to a facility.
The purpose of MFA is to restrict unauthorized users from entering a facility by adding an additional layer of authentication to the access control process. MFA enables businesses to monitor and help protect their most vulnerable information and networks. A good MFA strategy aims to strike a balance between user experience and increased workplace security.
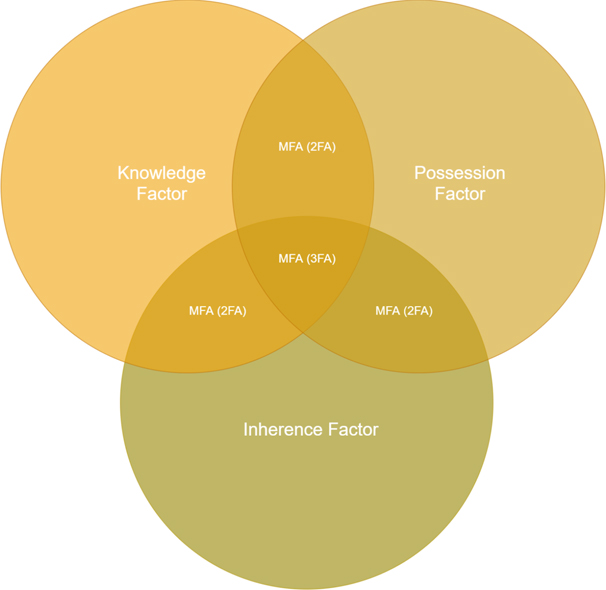
MFA uses two or more separate forms of authentication, including:
- Knowledge Factors. What the user knows (password and passcode)
- Possession Factors. What the user has (access card, passcode and mobile device)
- Inherence Factors. What is the user (biometrics)
MFA brings several benefits to the access system, including enhanced security and meeting compliance standards. Every user should face at least two layers of security before accessing any key.
9. Two-Man Rule or Three-Man Rule
For certain keys or key sets that are highly-sensitive, compliance regulations may require signatures from two or three individuals, one each from three separate departments, typically a drop-team member, a cage cashier and security officer. The cabinet door should not open until the system verifies that the user has permission for the specific key requested.

According to Gaming regulations, the physical custody of the keys, including duplicates, needed to access slot machine coin drop cabinets require the involvement of two employees, one of whom is independent of the slot department. The physical custody of the keys, including duplicates, needed to access the contents of the currency acceptor drop boxes require the physical involvement of employees from three separate departments. Furthermore, at least three count team members are required to be present when the currency acceptor and coin count room and other count keys are issued for the count and are at least three count team members required to accompany the keys until the time of their return.
10. Key Report
Gaming regulations require a number of different types of audits on a regular basis to assure the casino is in full compliance with regulations. For example, when employees sign the table game drop box keys in or out, Nevada Gaming Commission requirements call for maintenance of separate reports indicating the date, time, table game number, reason for access, and signature or electronic signature.
An “electronic signature” includes a unique employee PIN or card, or employee biometric identification validated and recorded through a computerized key security system. The key management system should have custom software that enables the user to set up all these and many other types of reports. A robust reporting system will greatly assist the business to track and improve processes, ensure employee honesty and minimize security risks.
11. Alert Emails
An alert email and text messaging function for key control systems provides management with timely alerts for any action that has been pre-programmed into the system. Key control systems incorporating this functionality can send emails to specific recipients. Emails can be sent securely from an external or Web-hosted email service. Time stamps are specific down to the second and emails are pushed to the server and delivered faster, providing accurate information that can be more effectively and quickly acted upon. For example, a key for a cash box may be pre-programmed so that management is sent an alert when this key is removed. An individual trying to leave the building without returning a key to the key cabinet can also be denied exit with their access card, prompting an alert to security.
12. Convenience
It is useful for authorized users to have quick access to specific keys or key sets. With instant key release, users simply enter their credentials and the system will know if they already have a specific key and the system will unlock for their immediate use. Returning keys is just as quick and easy. This saves time, reduces training and avoids any language barriers.

13. Extensible
It should also be modular and scalable, so the number of keys and range of functions can change and grow as the business changes.
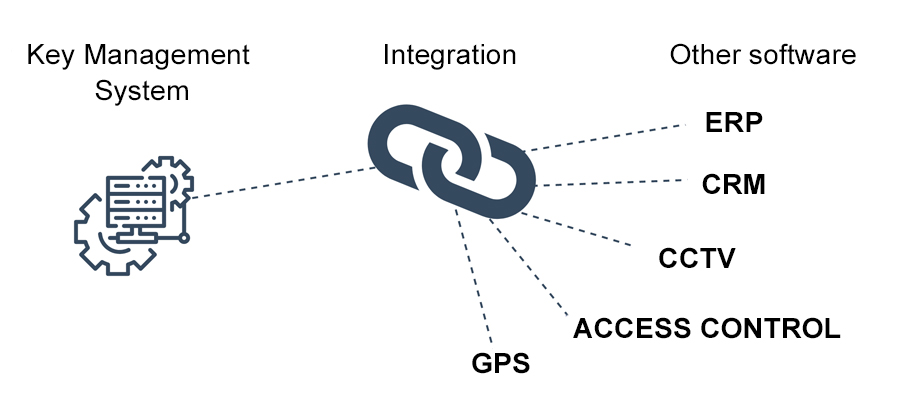
14. Ability to Integrate with Existing Systems
Integrated systems can help your team work on just one application to reduce switching for increased productivity. Maintain a single source of data by having data flow seamlessly from one system to another. In particular, setting up users and access rights is quick and easy when integrated with existing databases. Cost-wise, system integration reduces overhead to save time and reinvest it in other important areas of the business.
15. Easy to Use
Finally, it should be easy to use, as training time can be costly and many different employees will need to be able to access the system.
By keeping these elements in mind, a casino can manage their key control system wisely.
Post time: Jun-19-2023
