China Manufacture Mechanical Key Control System High-Security K26 Electronic Key Cabinet
How important is it to track keys?
Lost my key?
keys was stolen?
who holds the key?
who damaged the key?

Key tracking is critical, because they are a company asset that grants access to the most valuable areas and products. Since restricted keys can be confidently distributed, retailers should educate key holders of their importance and the key control policies surrounding them during key issuance. Use signature acknowledgments capturing their comprehension of this asset. Track who has keys, what they open, and audit them consistently. If an employee leaves, ask that they return all their company assets including keys. You can then be assured that the keys returned from a transitioning employee are the only keys they had.
Where should I start with key tracking?
K26 Intelligent Key cabinet for businesses with high demands for security. Key identification to monitor and control each individual key, behind a rated shell protection in cold rolled steel. The key system holds a maximum of 26 key positions but can be equipped with fewer positions and expand when business needs change.
Keylongest’s solution is simple. Keys, or keysets, are permanently attached using a tamper-proof security seal to a key Fob containing a uniquely identifiable electronic chip. The tagged iFob then locks into a receptor strip within the key cabinet until released by an authorized user.
Individual login via face recognition, fingerprint, PIN or select card reader when using RFID tags and cards for greater security. Key management is administered with the Keylongest Cloud Service, which means complete traceability of keys achieved of keys achieved using a functional and user-friendly interface.
Keylongest software retains a complete audit trail over every key transaction, giving you complete control and visibility over protected keys.
Benefits
Features
-
Reduce risk of misplaced and lost keys
- Key no longer need to be labeled, minimizing security risks if keys are lost
- Improved flexibility because keys are available 24/7 to authorized staff
- Keys are return quickly because users know they are both accountable and traceable
- Lower maintenance costs because users are taking better care of the equipment
- Improved utilization of equipment because staff can immediately report damage to equipment through the system (and the service department can respond more quickly)
- Lower operational costs with central key management as fewer resources are needed to distribute and manage large numbers of keys
- Increased visibility and organization of key use
- Reporting feature provides data useful to identify patterns such as vehicle performance, staff reliability and more
- Enhanced security benefits such as the ability to enable a system lockdown remotely, temporarily preventing all users from accessing the key cabinets
- Option to be a standalone solution with no need for a connection to an IT network
- Option to integrate with current systems such as access control, video surveillance, fire and safety, human resources, ERP systems, fleet management, time and attendance, and Microsoft Directory
1) Plug & Play solution with advanced RFID technology
2) Keys are available 24/7 to authorized staff only
3) Big, bright 7″Android touchscreen
4) 26 robust, long-life key fobs with security seals
5) Keys or key sets are individually locked in place
6) User, key, and access rights administration
7) PIN/Card/Face access to designated keys
8) Keys audit and reporting
9) Key reservation and application
10) Audible and visual alarms
11) Emergency Release System
12) Multi-system networking
Overview

①fill-in light – Auto Face Recognition Fill Light On/Off
②Facial reader – Register and identify users.
③7” Touch Screen – Built-in Android OS, and provide user-friendly interaction.
④Electric lock – The cabinet door.
⑤RFID Reader – Reading key tags and user cards.
⑥Status Light – status of the system. Green: OK; Red: Error.
⑦Key Slot – Key locking slots strip.

RFID KEY TAG
The Key Tag is the heart of the key management system. The RFID key tag can be used for identification and the triggering of an event on any RFID reader. The key tag enables easy access without waiting time and without tedious handing signing in and signing out.
What kind of software we have
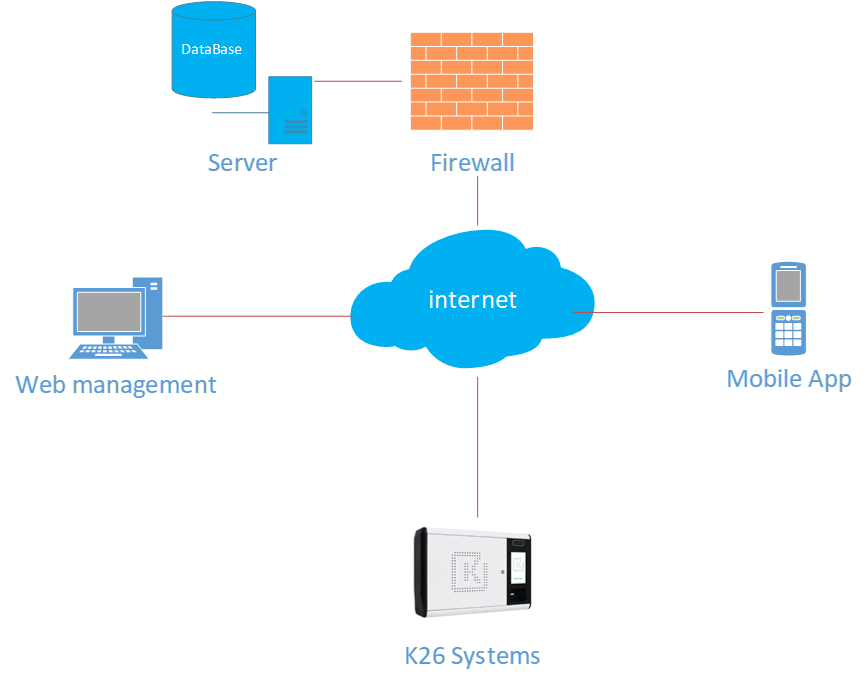
The cloud-based management system eliminates the need to install any additional programs and tools. It only needs an Internet connection to be available to understand any dynamics of the key, manage employees and keys, and grant employees the authority to use the keys and a reasonable use time.
Web-Based Management Software
The Landwell Web allows administrators to gain insight into all keys anywhere, anytime. It provides you with all the menus to config and track the whole solution.
Application on User Terminal
Having a User Terminal with a touchscreen on key cabinets provides users with an easy and fast way to remove and return their keys. It's user-friendly, nice, and highly customizable. In addition, it offers complete features to administrators for managing keys.
Handy Smartphone App
Landwell solutions provide a user-friendly smartphone app, downloadable from Play Store and App Store. It is not just made for users, but also for administrators, offering most functionalities to manage keys.
SOFTWARE FUNCTIONS
- Different Access Level
- Customizable User Roles
- Key Curfew
- Key Reservation
- Event Report
- Alert Email
- Two-Way Authorization
- Two-Man Verification
- Camera Capture
- Multi Language
- Automatic software update
- Multi-Systems Networking
- Release Keys by Administrators Off-site
- Personalized Customer Logo & Standby on the Display
Who need key management

Parameters
| Key Capacity | up to 26 keys / keysets |
| Body Materials | Steel + PC |
| Technology | RFID |
| Operating System | Based on Android |
| Display | 7” touch screen |
| Key Access | Face, Card, PIN code |
| Cabinet Dimensions | 566W X 380H X 177D (mm) |
| Weight | 17Kg |
| Power Supply | Input: 100~240V AC, Output: 12V DC |
| Power | 12V 2amp max |
| Moungting | Wall |
| Temperature | -20℃~55℃ |
| Network | Wi-Fi, Ethernet |
| Management | Networked or Standalone |
| Certificates | CE, Fcc, RoHS, ISO9001 |




